- TOP
- Data Center
- Managed Services
- IDS/IPS
IDS/IPS Intrusion Detection System/Intrusion Prevention System Service (IDS/IPS)
This service protects customers' information assets from external threats and risks.
The Intrusion Detection System/Intrusion Prevention System Service (IDS/IPS) detects signs of unauthorized access and attacks from outside as well as other serious threats, and protects customers' networks from such threats.
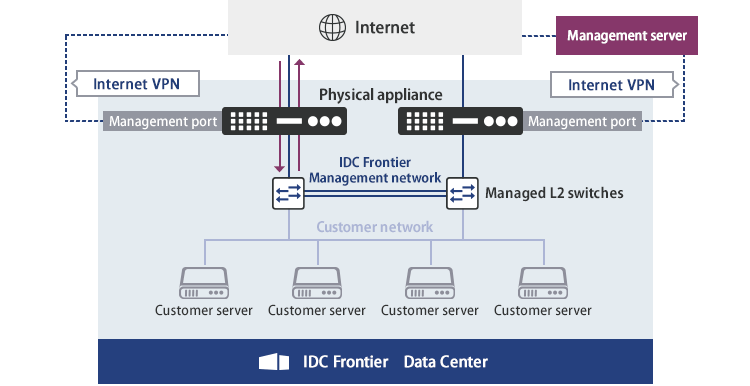
Two types are available. With the first type, a dedicated appliance is installed in the customer's Data Center (1 Gbps line or 10 Gbps line). With the second type, an agent is installed directly on the customer's server.
- Intrusion Detection System/
Intrusion Prevention System Service
(Physical appliance) - Intrusion Detection System/
Intrusion Prevention System Service
(Cloud One - Workload Security ™)
Physical appliance features
Provision of a dedicated appliance for customer environment (for a housing rack)
Equipment managed type provision
Helps reduce the security operation burdens of customers by providing managed solutions for physical appliance installation, configuration management, operation monitoring, and response to inquiries.
Provision of 10 Gbps-capable equipment
Two physical appliance models are available (1 Gbps and 10 Gbps). With 10 Gbps, customers can use the appliance reliably even with wide bandwidth.
No management server required
As the management server is provided by IDC Frontier, customers do not need to perform complicated management such as construction, operation, monitoring, and configuration management of the management server.
Physical appliance specifications
| Communication direction | Two-way communication | |
|---|---|---|
| Encrypted communication | Available (SSL option) | |
| Detection method | Manufacturer's standard signature | |
| Detection report | Auto-creation, auto-sending | |
| Operation (standard) | Equipment monitoring, configuration management, and equipment replacement in case of failure | |
| Security operation (option) |
Managed Security Service (MSS) Security Monitoring Center performs monitoring 24 hours a day, 365 days a year. Security analysts analyze threats based on various security alerts, analyze the presence or absence of attacks, degree of impact, and countermeasures, and notify customers about the analyses. In addition to notifications, security operations are optimized by performing blocking and other tuning. (Provided by SB Technology Corp.) |
|
Equipment specifications
| Item | 1Gbps Model | 10Gbps Model | ||
|---|---|---|---|---|
| Equipment | Redundant configuration (Active/Active) |
Redundant configuration (Active/Active) |
||
| External dimensions (width × depth × height) | 432 x 254 x 44mm (1U) | 432 x 380 x 44.45mm (1U) | ||
| Weight | 3.29Kg/1U | 6.4Kg/1U | ||
| Power supply redundancy | ◯ | ◯ | ||
| Fan redundancy | ◯ | ◯ | ||
| Maximum power consumption | 38.7W/1U | 189.2W/1U | ||
| IPS throughput performance *1 | 2.6Gbps | 12Gbps | ||
| Number of new firewall sessions *1 | 56,000 | 500,000 | ||
| Number of concurrent firewall sessions *1 | 1,500,000 | 7,800,000 | ||
| Interface *2 | Standard | 1000Base-T | 12 | 16 |
| Optional (for a fee) | 1000Base-T/ or 1000Base-SX/LX |
4 | - | |
| 1000Base-SX/LX | 4 | 8 | ||
| 10GBase-SR/LR | - | 4 | ||
*1: A catalog value; does not guarantee the processing capacity.
*2: The port and interface to be used are specified by IDC Frontier. Customers are not allowed to directly connect their own devices.
Benefits of introduction
- 24-hour monitoring and protection of important assets
- Reduces the introduction time and the required number of internal security personnel.
- Improved security system and lower total cost of ownership (TCO)
- Early warnings quickly block growing threats on the Internet and avoid unnecessary downtime.
- Security experts can optimize security operations 24 hours a day (optional).
Major configuration examples of Physical appliance
Features of Cloud One – Workload Security™
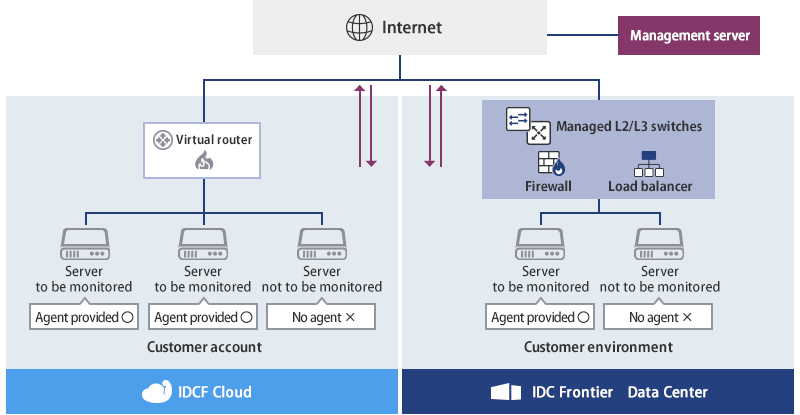
Provision of agent installed types (cloud housing rack)
Agent installation only
The customer only needs to install the agent on the server to be protected (physical or virtual server). The customer burden regarding security operations is reduced by the managed solutions including configuration management, operation monitoring, and response to inquiries.
Support for hybrid environments
The service can be used even if various infrastructures are mixed in an environment, including servers in Data Centers and virtual cloud servers.
No management server required
Since the management server provided is software as a service (SaaS) based, customers do not need to perform complicated management such as construction, operation, monitoring and configuration management of the management server.
Specifications of Cloud One – Workload Security™
| Communication direction | Two-way communication |
|---|---|
| Encrypted communication | Available (SSL option) |
| Detection method | Manufacturer's standard signature |
| Detection report | Auto-creation, auto-sending |
| Operation (standard) | Change monitoring, configuration management |
| Security operation (option) |
Managed Security Service (MSS) Security Monitoring Center performs monitoring 24 hours a day, 365 days a year. Security analysts analyze threats based on various security alerts, analyze the presence or absence of attacks, degree of impact, and countermeasures, and notify customers about the analyses. In addition to notifications, security operations are optimized by performing blocking and other tuning. (Provided by SB Technology Corp.) |
| Services used |
Trend Micro Cloud One – Workload Security ™ SaaS-based integrated cloud server security service provided by Trend Micro Incorporated (https://www.trendmicro.com/en_us/business/products/hybrid-cloud/cloud-one-workload-security.html  ) )
|
| Agent system requirements |
See below for the agent system requirements. (As of April 2021)
https://cloudone.trendmicro.com/docs/workload-security/agent-compatibility/ If using Linux OS, check the page below on the status of the kernel support. https://cloudone.trendmicro.com/docs/workload-security/agent-linux-kernel-support/
|
| Functions provided (IDS/IPS) | Protetion against vulnerabilities in OS and application using virtual patches |
| Change monitoring | Monitoring of changes to files, ports, etc. |
| Security log monitoring | Centralized monitoring of OS and middleware security events |
*: This service is provided as service by IDC Frontier, including necessary operation services based on Cloud One – Workload Security™ provided by Trend Micro Incorporated.
*: Customers are required to install/uninstall the agent on a target server.
*: Confirmation of configurations, changes, etc. are handled by IDC Frontier. Customers cannot check or change configurations directly from their management console.
Benefits of introduction
- 24-hour monitoring and protection of important assets
- Reduces the introduction time and the required number of internal security personnel.
- Improved security system and lower total cost of ownership (TCO)
- Early warnings quickly block growing threats on the Internet and avoid unnecessary downtime.
- Security experts can optimize security operations 24 hours a day (optional).
Major configuration examples of
Cloud One – Workload Security™
Company names and product names mentioned are registered trademarks or trademarks of each company.
